AWS CSPM
This guide describes how to setup an IAM user, and assign policies like Read only access, and Security Audit for TraQez Security Scanner to perform Security Checks, Misconfigurations, Compliance Checks, Asset Inventory discovery, Resource discovery.
Generating the access secret key and access secret id
- Login into your AWS Account and go to IAM Dashboard.
- Go to
Policies(look at Access Management) and click on Create policy. - Under Specify Permissions, click on JSON as policy editor.
- To run TraQez Security Scanner, you will need a policy with read only access permissions. Click here to download the Policy AWS Policy For TraQez. Copy the contents of the JSON file and paste in the Policy editor.
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"account:Get*",
"appstream:Describe*",
"appstream:List*",
"backup:List*",
"cloudtrail:GetInsightSelectors",
"codeartifact:List*",
"codebuild:BatchGet*",
"cognito-idp:GetUserPoolMfaConfig",
"dlm:Get*",
"drs:Describe*",
"ds:Get*",
"ds:Describe*",
"ds:List*",
"dynamodb:GetResourcePolicy",
"ec2:GetEbsEncryptionByDefault",
"ec2:GetSnapshotBlockPublicAccessState",
"ec2:GetInstanceMetadataDefaults",
"ecr:Describe*",
"ecr:GetRegistryScanningConfiguration",
"elasticfilesystem:DescribeBackupPolicy",
"glue:GetConnections",
"glue:GetSecurityConfiguration*",
"glue:SearchTables",
"lambda:GetFunction*",
"logs:FilterLogEvents",
"lightsail:GetRelationalDatabases",
"macie2:GetMacieSession",
"s3:GetAccountPublicAccessBlock",
"shield:DescribeProtection",
"shield:GetSubscriptionState",
"securityhub:BatchImportFindings",
"securityhub:GetFindings",
"ssm:GetDocument",
"ssm-incidents:List*",
"support:Describe*",
"tag:GetTagKeys",
"wellarchitected:List*",
"acm:DescribeCertificate",
"acm:ListCertificates",
"cloudformation:DescribeStacks",
"cloudformation:GetStackPolicy",
"cloudformation:GetTemplate",
"cloudformation:ListStacks",
"cloudtrail:DescribeTrails",
"cloudtrail:GetEventSelectors",
"cloudtrail:GetTrailStatus",
"cloudwatch:DescribeAlarms",
"cloudfront:ListDistributions",
"codebuild:BatchGetProjects",
"codebuild:ListProjects",
"cognito-identity:DescribeIdentityPool",
"cognito-identity:ListIdentityPools",
"cognito-idp:DescribeUserPool",
"cognito-idp:ListUserPools",
"config:DescribeConfigRules",
"config:DescribeConfigurationRecorderStatus",
"config:DescribeConfigurationRecorders",
"directconnect:DescribeConnections",
"dynamodb:DescribeContinuousBackups",
"dynamodb:DescribeTable",
"dynamodb:ListBackups",
"dynamodb:ListTables",
"dynamodb:ListTagsOfResource",
"ec2:DescribeCustomerGateways",
"ec2:DescribeFlowLogs",
"ec2:DescribeImages",
"ec2:DescribeInstanceAttribute",
"ec2:DescribeInstances",
"ec2:DescribeNetworkAcls",
"ec2:DescribeNetworkInterfaceAttribute",
"ec2:DescribeNetworkInterfaces",
"ec2:DescribeRegions",
"ec2:DescribeRouteTables",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSnapshotAttribute",
"ec2:DescribeSnapshots",
"ec2:DescribeSubnets",
"ec2:DescribeVolumes",
"ec2:DescribeVpcPeeringConnections",
"ec2:DescribeVpcs",
"ec2:DescribeVpnConnections",
"ec2:DescribeVpnGateways",
"ec2:GetEbsDefaultKmsKeyId",
"ecr:DescribeImages",
"ecr:DescribeRepositories",
"ecr:GetLifecyclePolicy",
"ecr:GetRepositoryPolicy",
"ecr:ListImages",
"ecs:DescribeClusters",
"ecs:ListAccountSettings",
"ecs:ListClusters",
"eks:DescribeCluster",
"eks:ListClusters",
"elasticache:DescribeCacheClusters",
"elasticache:DescribeCacheParameterGroups",
"elasticache:DescribeCacheSecurityGroups",
"elasticache:DescribeCacheSubnetGroups",
"elasticfilesystem:DescribeFileSystems",
"elasticfilesystem:DescribeMountTargetSecurityGroups",
"elasticfilesystem:DescribeMountTargets",
"elasticfilesystem:DescribeTags",
"elasticloadbalancing:DescribeListeners",
"elasticloadbalancing:DescribeLoadBalancerAttributes",
"elasticloadbalancing:DescribeLoadBalancerPolicies",
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeSSLPolicies",
"elasticloadbalancing:DescribeTags",
"elasticmapreduce:DescribeCluster",
"elasticmapreduce:ListClusters",
"guardduty:GetDetector",
"guardduty:ListDetectors",
"iam:GenerateCredentialReport",
"iam:GetAccountPasswordPolicy",
"iam:GetCredentialReport",
"iam:GetGroup",
"iam:GetGroupPolicy",
"iam:GetLoginProfile",
"iam:GetPolicy",
"iam:GetPolicyVersion",
"iam:GetRole",
"iam:GetRolePolicy",
"iam:GetUserPolicy",
"iam:ListAccessKeys",
"iam:ListAttachedRolePolicies",
"iam:ListEntitiesForPolicy",
"iam:ListGroupPolicies",
"iam:ListGroups",
"iam:ListGroupsForUser",
"iam:ListInstanceProfilesForRole",
"iam:ListMFADevices",
"iam:ListPolicies",
"iam:ListRolePolicies",
"iam:ListRoleTags",
"iam:ListRoles",
"iam:ListUserPolicies",
"iam:ListUserTags",
"iam:ListUsers",
"iam:ListVirtualMFADevices",
"kms:DescribeKey",
"kms:GetKeyPolicy",
"kms:GetKeyRotationStatus",
"kms:ListAliases",
"kms:ListGrants",
"kms:ListKeys",
"lambda:GetFunctionConfiguration",
"lambda:GetPolicy",
"lambda:ListFunctions",
"logs:DescribeMetricFilters",
"rds:DescribeDBClusterSnapshotAttributes",
"rds:DescribeDBClusterSnapshots",
"rds:DescribeDBClusters",
"rds:DescribeDBInstances",
"rds:DescribeDBParameterGroups",
"rds:DescribeDBParameters",
"rds:DescribeDBSecurityGroups",
"rds:DescribeDBSnapshotAttributes",
"rds:DescribeDBSnapshots",
"rds:DescribeDBSubnetGroups",
"rds:ListTagsForResource",
"redshift:DescribeClusterParameterGroups",
"redshift:DescribeClusterParameters",
"redshift:DescribeClusterSecurityGroups",
"redshift:DescribeClusters",
"route53:ListHostedZones",
"route53:ListResourceRecordSets",
"route53domains:ListDomains",
"s3:GetBucketAcl",
"s3:GetBucketLocation",
"s3:GetBucketLogging",
"s3:GetBucketPolicy",
"s3:GetBucketTagging",
"s3:GetBucketVersioning",
"s3:GetBucketWebsite",
"s3:GetEncryptionConfiguration",
"s3:GetBucketPublicAccessBlock",
"s3:ListAllMyBuckets",
"secretsmanager:ListSecrets",
"secretsmanager:DescribeSecret",
"secretsmanager:GetResourcePolicy",
"ses:GetIdentityDkimAttributes",
"ses:GetIdentityPolicies",
"ses:ListIdentities",
"ses:ListIdentityPolicies",
"ssm:DescribeParameters",
"ssm:GetParameters",
"sns:GetTopicAttributes",
"sns:ListSubscriptions",
"sns:ListTopics",
"sqs:GetQueueAttributes",
"sqs:ListQueues",
"glue:GetTriggers",
"ses:DescribeActiveReceiptRuleSet",
"athena:GetWorkGroup",
"logs:DescribeLogGroups",
"logs:DescribeMetricFilters",
"elastictranscoder:ListPipelines",
"elasticfilesystem:DescribeFileSystems",
"servicequotas:ListServiceQuotas"
],
"Resource": "*",
"Effect": "Allow",
"Sid": "AllowMoreReadForProwler"
},
{
"Effect": "Allow",
"Action": [
"apigateway:GET"
],
"Resource": [
"arn:aws:apigateway:*::/restapis/*",
"arn:aws:apigateway:*::/apis/*"
]
}
]
}
- Click Next and Give it the Policy name
traqez@security-check-v1.0. Click on Create policy - Next Go to
Users(present in Access Management). Click on Create user. Name the user astraqez@cloudscan-1Create a new IAM user. Note: The optionProvide user access to the AWS Management Console - optionalshould NOT be checked. It's not necessary. - Click Next, and Select
Attach policies directly. Search fortraqez@security-check-v1.0and select it. Also additionally you need to Select the following.arn:aws:iam::aws:policy/SecurityAudit(Search forSecurityAudit)arn:aws:iam::aws:policy/job-function/ViewOnlyAccess(Search forViewOnlyAccess)
- Click on Next. Verify that total 3 policies are attached. Click on Create user. Refer to
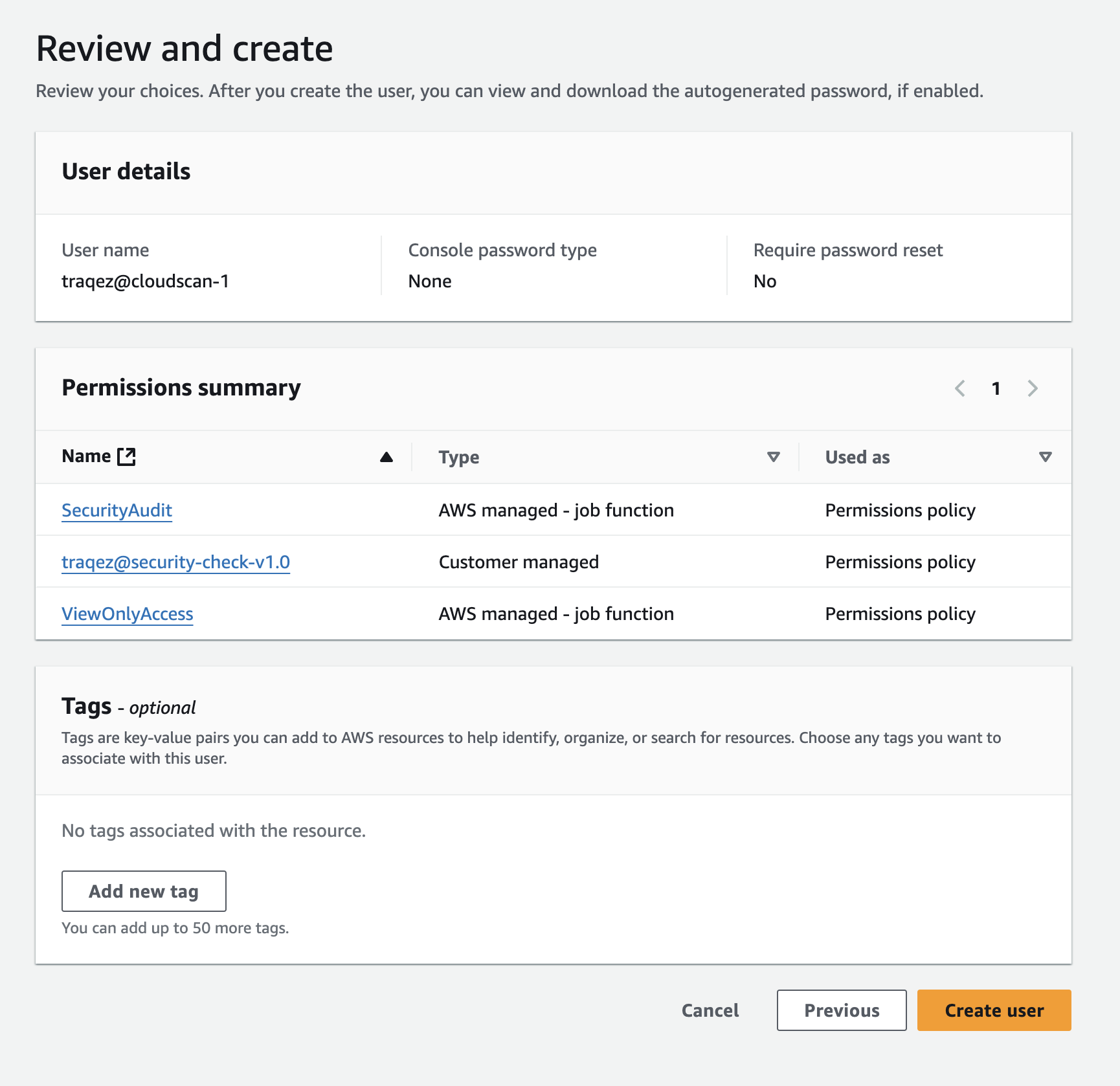
- Now search for the new user
traqez@cloudscan-1and click on the user. Go to theSecurity credentialstab of the newly created user. - Look for
Access keyssection and click onCreate Access key. - Select the
Third-party serviceoption and check the Confirmation box. Click Next - Description is Optional and click on Create access key.
- Copy the Access key and Secret access key which looks like as shown below.
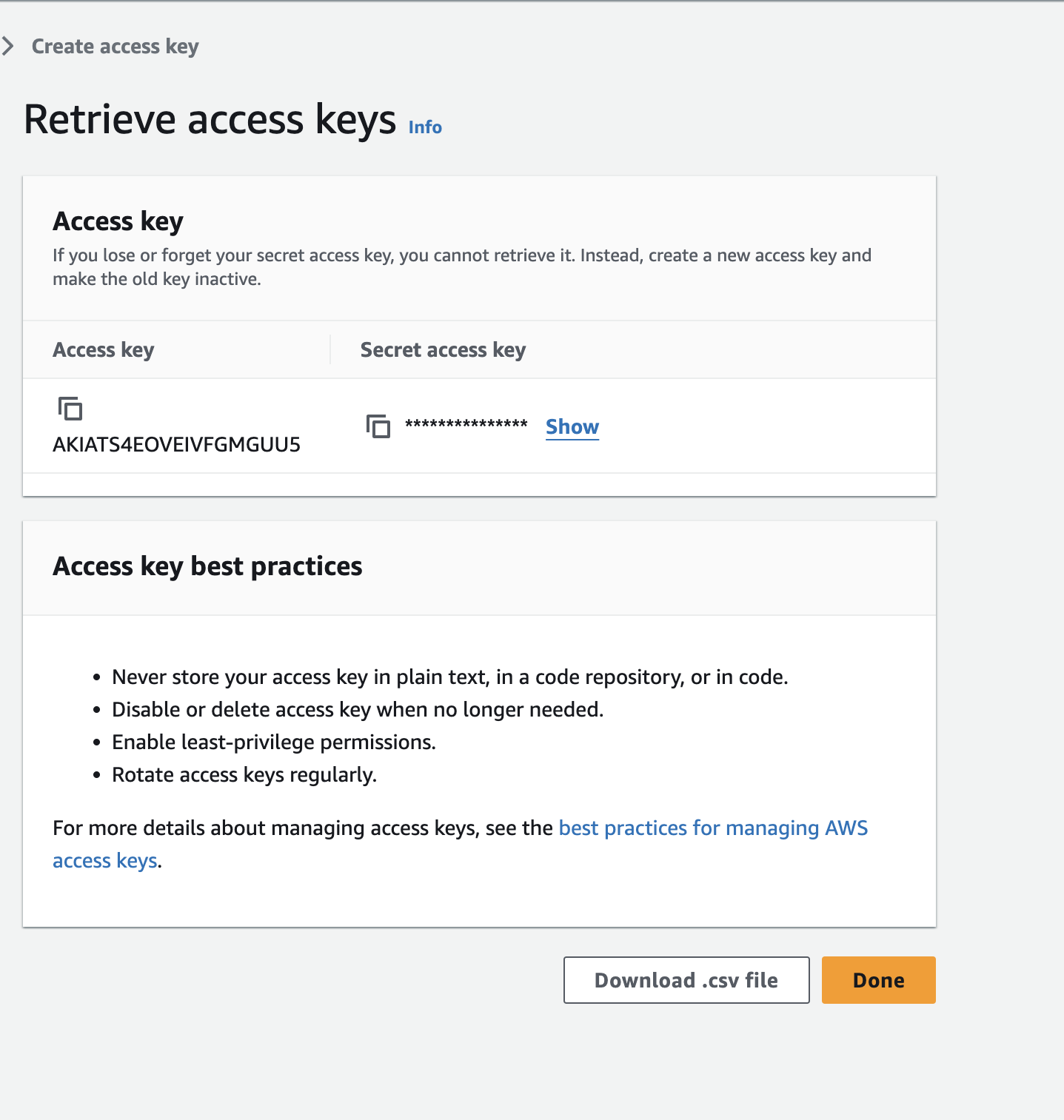
- Paste the copied Access Secret Id into the
Access IDtextbox in the connectors dashboard within Cloud Security (CSPM). - Paste the copied Access Secret key into the
Access Secret Keytextbox in the connectors dashboard within Cloud Security (CSPM). - AWS Account Id is also required. Click on the
"AWS root account"user displayed at the top right, and copy the AWSAccount IDshown.
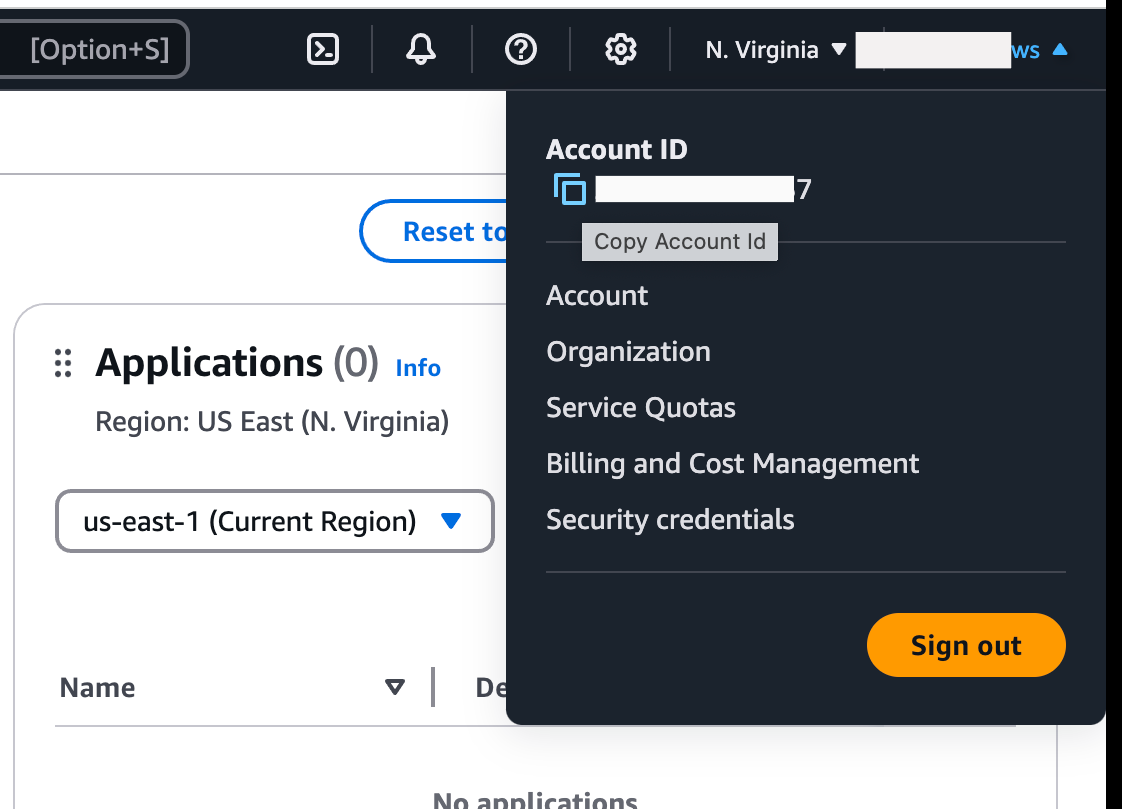
- Paste the copied AWS Account Id into the
Account IDtextbox in the connectors dashboard within Cloud Security (CSPM).
Creating new Connector.
Fill in the remaining connector details using the collected information: Account Id, Access Secret ID, and Access Secret Key.
- Select the cloud Provider:
AWSfrom the dropdown. - Enter the desired
Connector Name,DescriptionandTags. - Scan Settings: Configure the frequency of your scans and email report settings in this section. You can modify these settings at any time, even after the scan has been created.
- Configure periodic cloud security scanning by selecting the
Perform periodic scanning for new Connectoroption:- Daily: Scan assets daily at a specified time.
- Weekly: Scan assets weekly on a chosen day (e.g., Friday, Saturday) at a specified time.
- Bi-Weekly: Scan assets every other week on a chosen day at a specified time.
- Monthly: Scan assets monthly on a chosen day within the first week of the month at a specified time.
- Schedule a one-time scan for a future date and time by selecting the
Schedule Scan at given time and run only once.option. The scan will execute at the specified time based on your configured user timezone.
Note: When enabling periodic/continuous scanning, the configured scan time will be executed in UTC Timezone. For example, if you schedule a scan for 4:00 am, it will run at 4:00 am UTC, not 4:00 in your local timezone.
- Scan Options: Customize the behavior of the vulnerability scanner and refine your results using the following options:
- Save all scan artifacts for later reference. Select this option to store all scan-related data, including logs and evidence, for future reference. This will retain raw data generated during the scan.
- Save vulnerabilities with information/log level. Log information level messages from the vulnerability scanner which includes enumeration information, service information etc. Also useful for asset discovery and mapping.
- Scan for all supported services across your cloud environment. Enable this checkbox to scan all supported services within AWS (around 60+ services are supported.) or customise what services need to be scanned by selecting the dropdown
Select custom services for cloud environment.
- Fill in the
Scan Credentialssection with the collected information:- Account ID
- Access ID
- Access Secret Key
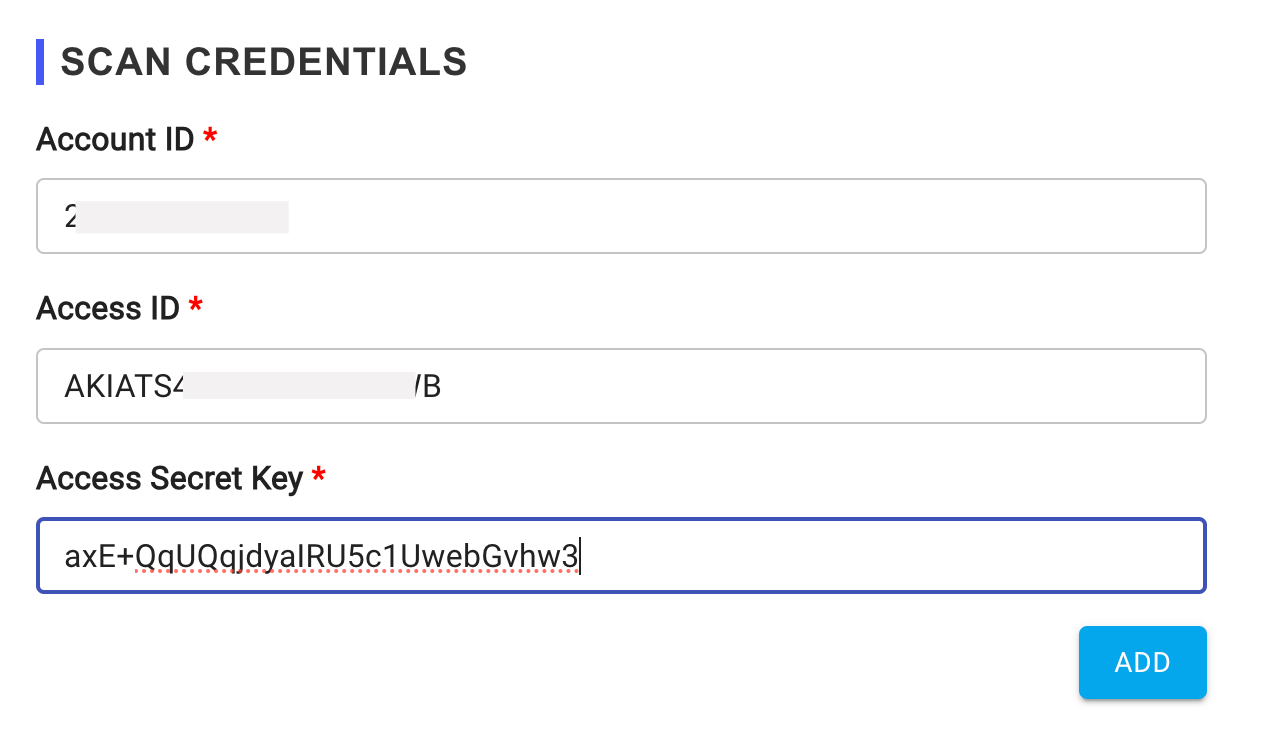
- Complete the scan credentials configuration.
Supported AWS services for Scan
- ec2
- iam
- rds
- cloudwatch
- s3
- cognito
- cloudtrail
- cloudfront
- opensearch
- glue
- vpc
- sagemaker
- elbv2
- ecs
- redshift
- neptune
- guardduty
- elb
- dynamodb
- awslambda
- kafka
- elasticache
- autoscaling
- apigateway
- wafv2
- networkfirewall
- efs
- codebuild
- shield
- eks
- ecr
- documentdb
- dms
- directoryservice
- organizations
- backup
- secretsmanager
- route53
- kms
- eventbridge
- appstream
- account
- lightsail
- ssm
- sns
- emr
- athena
- acm
- workspaces
- trustedadvisor
- sqs
- macie
- inspector2
- config
- cloudformation
- apigatewayv2
- accessanalyzer
- wellarchitected
- storagegateway
- ssmincidents
- securityhub
- resourceexplorer2
- glacier
- fms
- drs
- dlm
- codeartifact