Cloud Security Posture Management (CSPM)
The Cloud Security Posture Management (CSPM) module provides continuous monitoring and automated auditing of your cloud environments – AWS, Azure, and GCP – to detect and remediate misconfigurations and compliance risks across services, accounts, and regions.
It continuously evaluates your resources against 1000+ predefined rules based on industry standards like CIS Benchmarks, NIST 800-53, SOC 2, HIPAA, and GDPR, ensuring your cloud configurations remain secure and compliant.
How It Works
The process begins by connecting your cloud environments via secure read-only connectors for AWS, Azure, and GCP. Once connected, the system automatically performs a configuration audit that includes:
- Resource Discovery: Identifies and maps all resources across your connected accounts, including compute, storage, network, and IAM components.
- Configuration Evaluation: Validates each resource against security best practices and compliance benchmarks.
- Rule Evaluation: Each rule check results in one of the following statuses:
- ✅ Passed: Resource is securely configured.
- ❌ Failed: Resource is misconfigured (potential risk).
- Severity Assessment: Every misconfiguration is rated as Critical, High, Medium, or Low, helping prioritize remediation.
- Cloud Resource Context: For each finding, CSPM shows detailed information such as:
- Resource type and name
- Service and category (e.g., S3 → Storage → Bucket)
- Cloud region
- Associated account ID and connector name
Example: Misconfigured S3 bucket (Public Access Enabled) → Region:
us-east-1→ Severity:High
Requirements
- Connector Requirement: Requires at least one configured connector per cloud provider (AWS, Azure, GCP).
- Permissions: Connectors must have read-only permissions to allow inventory collection and configuration assessment.
- Supported Providers:
- AWS
- Microsoft Azure
- Google Cloud Platform (GCP)
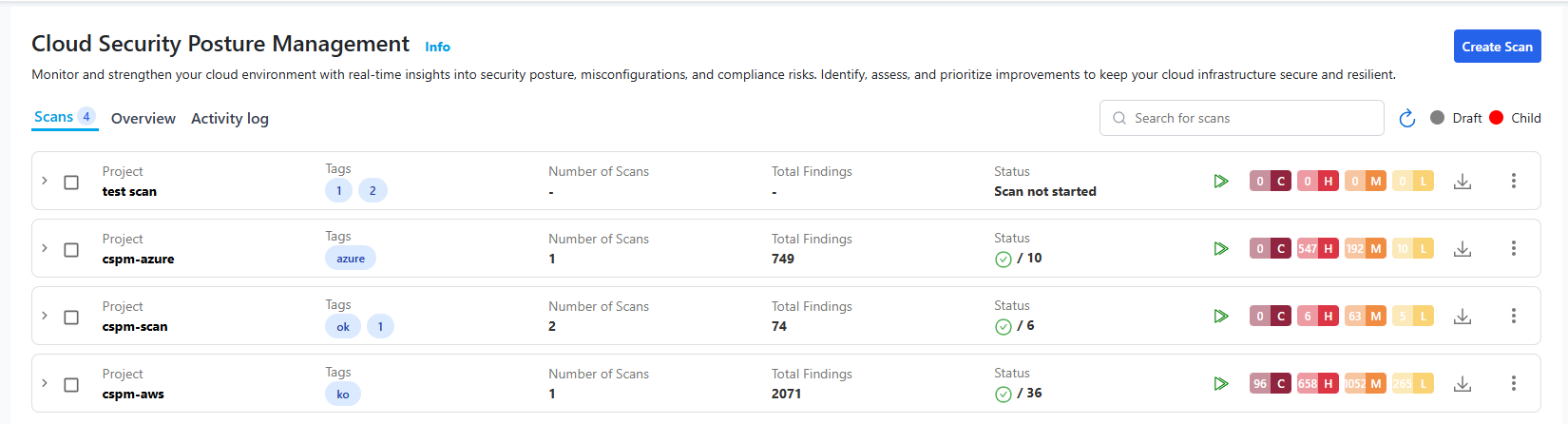
Creating a New Scan
- To initiate a new posture assessment, locate the
Create Scanbutton in the top-right corner of the CSPM dashboard and click on it.
To view a reference image of the create scan button, click here to expand.
- A slide-over panel appears, prompting you to select your cloud provider:
- AWS (default)
- Azure
- GCP
- You'll then be prompted to either reuse existing connectors or manually enter credentials.
To view a reference image of selecting cloud providers, click here to expand.
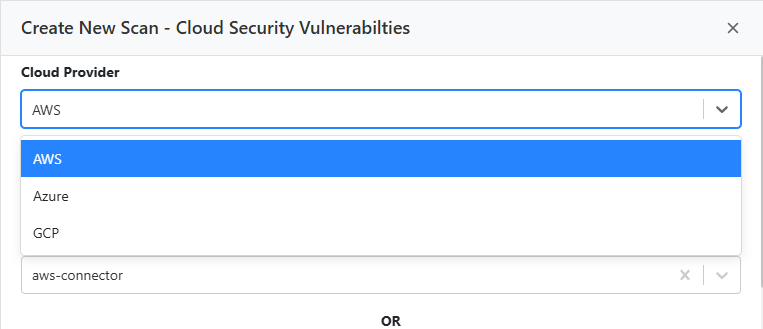
Reuse Existing Connector
Use existing credentials already configured in the Cloud Security (CSPM) → Connector Dashboard. Select a connector from the dropdown to proceed with posture scanning.
Note: For instructions on creating a connector, see Cloud Security (CSPM) → Connector Dashboard documentation.
Manual Credential Entry
Manually input the following credentials for your selected provider:
- AWS: Account ID, Access Key, Secret Key
- Azure: Subscription ID, Tenant ID, Client ID, Client Secret
- GCP: Credentials JSON file
Once credentials are verified, click Import Resources to pull all resource metadata from your cloud account.
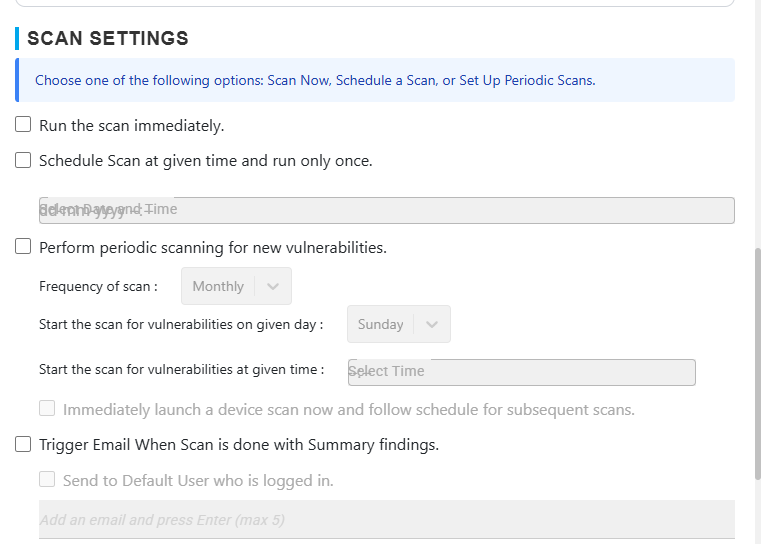
- Next, configure the following scan details:
- Scan Name (required)
- Description (optional)
- Tags (optional)
- Schedule Settings
- Rule Set / Benchmark Selection (CIS, NIST, SOC 2, etc.)
Note: You can run scans ad-hoc or schedule periodic posture assessments (Daily, Weekly, Monthly, etc.).
To view a reference image of scan configuration options, click here to expand.
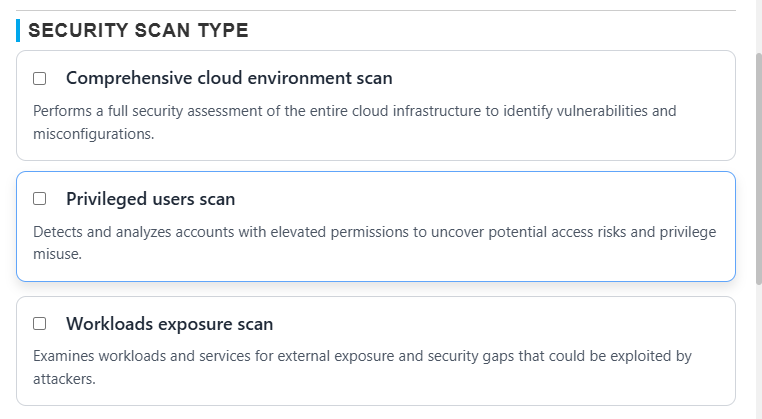
Security Scan Type / Scanner Selection
Each CSPM scan can be configured to target a specific subset of your cloud environment based on your security focus or compliance goals. The following scan types are supported:
| Scan Type | Description |
|---|---|
| Comprehensive Cloud Environment Scan | Performs a full security assessment across all supported services and configurations in your cloud account. Ideal for complete posture visibility and compliance benchmarking. |
| Privileged Users Scan | Focuses exclusively on IAM, roles, and policies to detect over-privileged accounts, missing MFA, unused credentials, and other identity-based risks. |
| Workloads Exposure Scan | Scans compute-related assets such as EC2 instances, virtual machines, Kubernetes clusters, and managed databases, evaluating exposure to public networks, misconfigured firewalls, or missing encryption. |
Tip: Selecting a focused scan type helps reduce runtime and narrow the scope to specific compliance or operational needs.
To view a reference image of scan type selection, click here to expand.
Managing Existing Scans
After creating a scan, navigate to the Posture Assessments list to view all created scans in a collapsible, accordion-style layout.
Each scan entry displays:
- Project (Scan Name)
- Cloud Provider
- Connector Used
- Scan Status (Done, Failed, Running, Partially Done)
- Last Scan Findings (Passed/Failed count)
- Severity Summary (Critical, High, Medium, Low)
Use the Run icon to manually execute a scan, or use the three-dot menu to edit or delete.
Editing Scans
Editing allows you to modify:
- Scan Name / Description / Tags
- Rule Set / Benchmark
- Scheduling options
Note: The selected cloud provider cannot be changed once a scan is created.
Viewing Scan Results
Click on any Project (Scan Name) to view detailed scan results. The CSPM results dashboard consists of four main tabs:
- Summary
- Misconfigurations (default tab)
- Attack Surface
- History
- Resource Inventory
Misconfigurations Tab
This is the default tab and provides a list of all detected misconfigurations across accounts and services.
Each row includes:
- Rule Name and ID
- Resource Affected
- Cloud Provider
- Region
- Severity
- Status (Passed / Failed)
- Compliance Mappings (CIS, NIST, SOC 2, etc.)
To view a reference image of misconfigurations list, click here to expand.
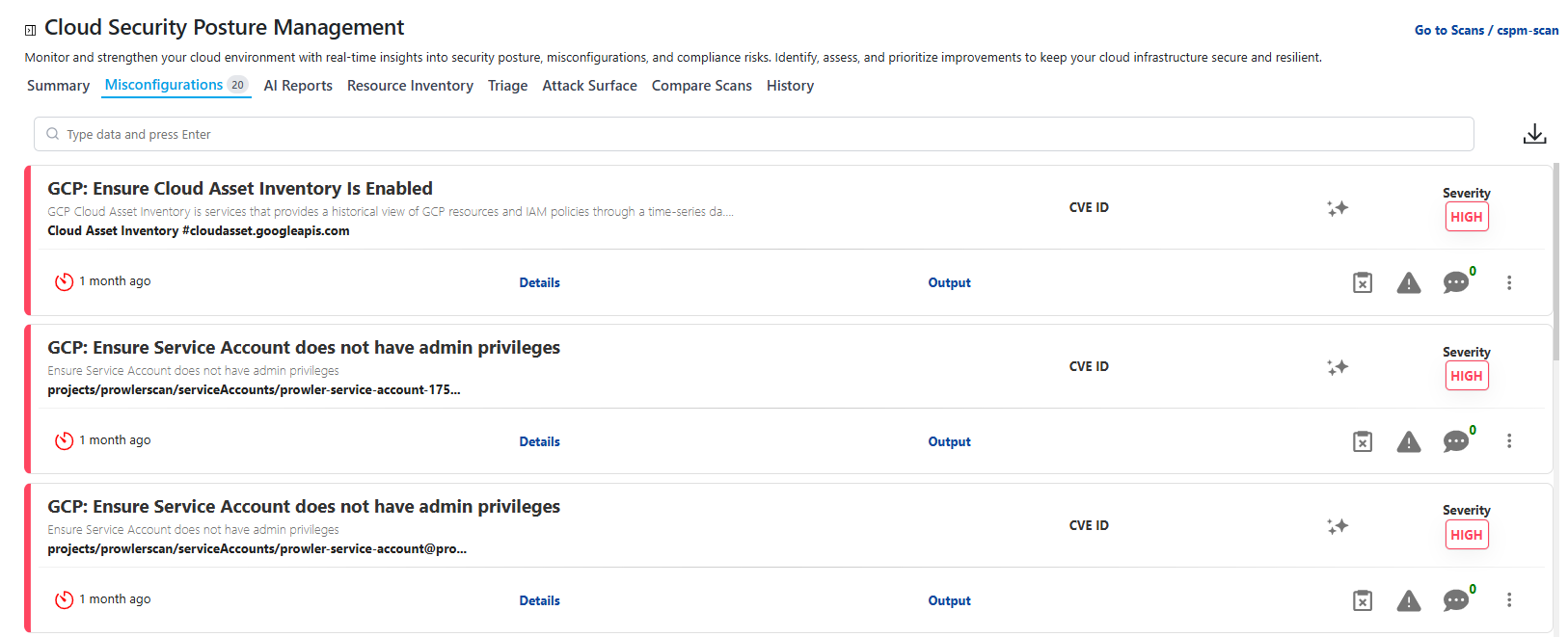
Click Details to expand an accordion containing:
- Rule Description
- Detected Issue Explanation
- Risk and Impact
- Remediation Steps
- Compliance Mapping
- References to Provider Docs
Summary Tab
The Summary Tab aggregates results from all findings and provides a high-level overview of your cloud posture.
Includes:
- Total Findings: Overall count of checks performed
- Passed vs Failed: Ratio of secure vs misconfigured resources
- Severity Distribution: Critical / High / Medium / Low breakdown
- Region-wise Misconfigurations: Interactive map or bar chart by region
- Service-based Misconfigurations: Stacked bar graph of top affected services (e.g., EC2, S3, IAM)
- Top Failing Rules: Frequently violated policies
Attack Surface
The Attack Surface Tab visually maps your entire cloud environment hierarchy.
Example hierarchy:
AWS Account
├── Compute (EC2, Lambda)
├── Storage (S3, EBS)
├── Network (VPC, Security Groups)
└── IAM (Users, Roles, Policies)
This hierarchical visualization helps identify relationships between misconfigured assets and their dependent services.
Resource Inventory
The Resource Inventory Tab acts as a centralized view of all discovered cloud resources across providers.
Each record includes:
- Resource Name and ID
- Resource Type
- Service / Category
- Cloud Provider
- Region
- Linked Misconfiguration (if any)
History Tab
The History Tab provides visibility into all previous posture scans, including scan duration, status, and findings summary.
Each entry includes:
- Scan Time
- Duration
- Status (Done / Failed)
- Passed / Failed Count
- Error Logs and Evidence
You can access raw scan artifacts (JSON, HTML, LOG, or CSV) via the Artifacts option in the three-dot menu.
Deleting a Scan
To delete a posture scan:
- Click the three-dot menu next to a scan → select Delete.
- Confirm by typing
DELETEin the popup confirmation dialog.
To view a reference image of deleting a scan, click here to expand.
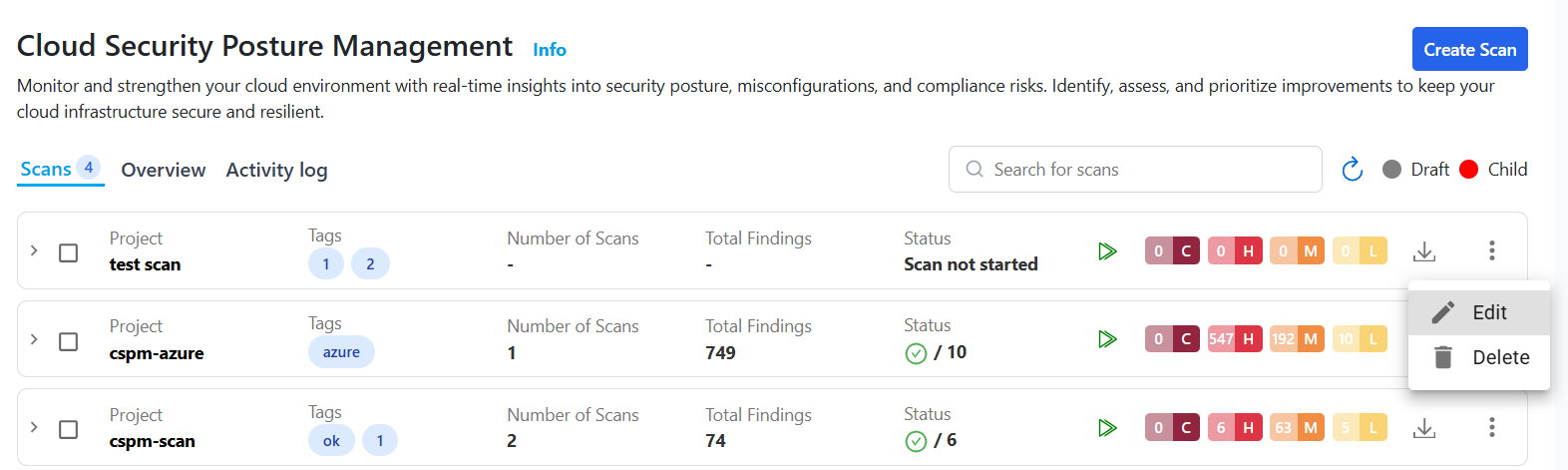
Scanning Limits
- Each scan can evaluate up to 500 resources per connector in a single run.
- If your account contains more than 500 resources, the system will automatically split them into smaller groups (child scans).
- Parent scans act as containers for these child scans.
Launching a Scan
To manually run a posture scan:
- Click the Run icon next to a scan in the list.
- This triggers an immediate cloud audit using the selected connector and benchmark rules.
Scheduled scans will automatically execute at configured intervals (Daily, Weekly, etc.).
Email Notifications
Email alerts are automatically sent when:
- A posture scan starts or completes.
- A critical misconfiguration is detected.
- A scheduled scan fails or misses execution.
Troubleshooting Scan Errors
If a scan fails, one of the following statuses may appear:
- Scan Submit Error: Scanner service temporarily unavailable or quota exceeded.
- Failed: Misconfiguration check failed or timed out.
To diagnose:
- Open the scan.
- Navigate to the History Tab.
- Click the three-dot menu.
- Select Errors.
A detailed stack trace or message will appear for troubleshooting. Share this log with the TraQez Support Team for resolution.
Supported Services for Cloud Providers
Each CSPM scan type leverages the supported services available within your connected cloud account. This ensures complete coverage for posture management, compliance checks, and misconfiguration detection. You can reference these in your AWS, Azure, and GCP Connector Setup documentation using this section link.
Quick Reference Summary
| Cloud Provider | Supported Services (Examples) | Example Categories |
|---|---|---|
| AWS | EC2, S3, RDS, IAM, CloudTrail, CloudFront, EKS, GuardDuty, Config, Lambda | Compute, Storage, Network, IAM, Monitoring |
| Azure | Virtual Machines, Storage, SQL Server, Defender, Entra (AD), Key Vault, AKS, Policy | Compute, Storage, Network, IAM, Security |
| GCP | Compute, Cloud Storage, Cloud SQL, IAM, GKE, KMS, BigQuery, Cloud Logging | Compute, Storage, Network, IAM, Observability |
Supported AWS Services for Scan
- ec2
- iam
- rds
- cloudwatch
- s3
- cognito
- cloudtrail
- cloudfront
- opensearch
- glue
- vpc
- sagemaker
- elbv2
- ecs
- redshift
- neptune
- guardduty
- elb
- dynamodb
- awslambda
- kafka
- elasticache
- autoscaling
- apigateway
- wafv2
- networkfirewall
- efs
- codebuild
- shield
- eks
- ecr
- documentdb
- dms
- directoryservice
- organizations
- backup
- secretsmanager
- route53
- kms
- eventbridge
- appstream
- account
- lightsail
- ssm
- sns
- emr
- athena
- acm
- workspaces
- trustedadvisor
- sqs
- macie
- inspector2
- config
- cloudformation
- apigatewayv2
- accessanalyzer
- wellarchitected
- storagegateway
- ssmincidents
- securityhub
- resourceexplorer2
- glacier
- fms
- drs
- dlm
- codeartifact
Supported Azure Services for Scan
- defender
- app
- entra
- monitor
- sqlserver
- storage
- network
- keyvault
- postgresql
- vm
- mysql
- aks
- cosmosdb
- iam
- policy
- appinsights
Supported GCP Services for Scan
- compute
- iam
- logging
- dns
- cloudstorage
- bigquery
- apikeys
- kms
- gke
- gcr
- dataproc
- artifacts