Container Scanning
The Container Scanning module in DeepTraQ identifies security vulnerabilities, configuration issues, and compliance risks across container images and registries. It ensures your containerized workloads remain secure from build-time to runtime by automatically detecting:
- Vulnerable OS packages and libraries (CVE-based)
- Misconfigured Dockerfiles or image manifests
- Weak permissions, plaintext secrets, and insecure base images
- Exposures in container runtime environments (Kubernetes, ECS, AKS, GKE, etc.)
DeepTraQ supports scanning both local images and remote container registries such as:
- Amazon ECR
- Azure Container Registry (ACR)
- Google Container Registry (GCR)
- Docker Hub
- Harbor and other private registries
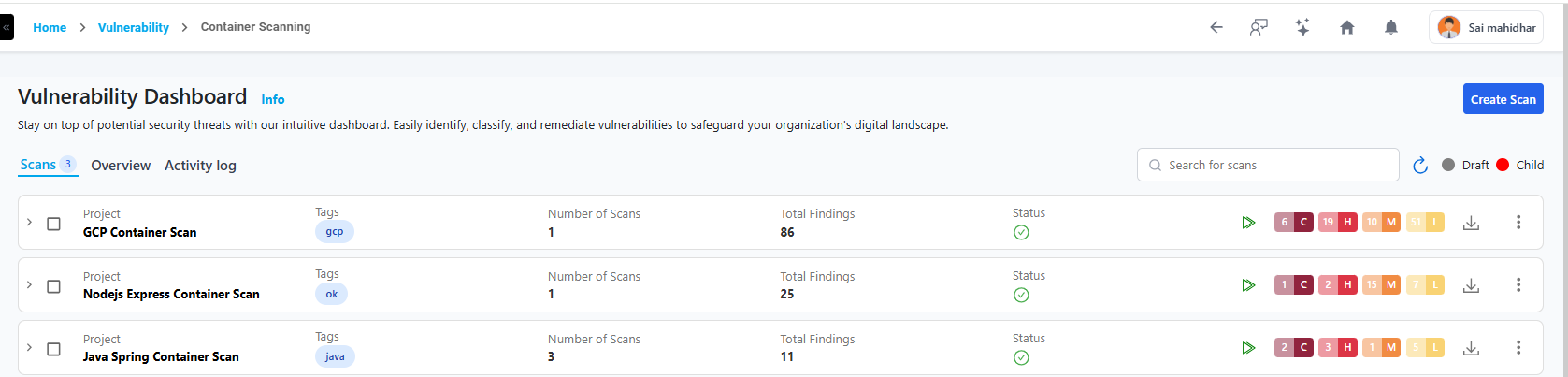
View placeholder image for Container Dashboard
How It Works
- Discovery Phase – DeepTraQ connects to your configured registries or local repositories to list available images and tags.
- Extraction Phase – Image layers are unpacked and analyzed for OS packages, dependencies, and configurations.
- Vulnerability Detection – The scanner cross-references with multiple CVE databases and container advisories (NVD, distro-specific, etc.).
- Configuration Analysis – Dockerfile, ENV variables, and permissions are reviewed for security best practices.
- Results & Insights – Findings are mapped to CVE, CWE, NIST 800-53, and CIS Docker/Kubernetes Benchmarks.
Container scanning can be run manually or scheduled automatically as part of CI/CD integration to detect issues before deployment.
Requirements
| Requirement | Description |
|---|---|
| Registry Credentials | Read access to container registries (ECR, ACR, GCR, Docker Hub, Harbor, etc.) |
| Image Name / Tag | Specific image and tag to scan (e.g., nginx:1.25-alpine) |
| Agent Permissions | Network and registry API access for pulling metadata |
| For CI/CD Scans | DeepTraQ scanning token or API key configured in pipeline |
| Supported Formats | Docker v2, OCI-compliant images |
If using a private registry, ensure that credentials are stored securely in the connector setup before starting a scan.
Creating a Scan
- Navigate to Container Scanning from the main dashboard.
- Click Create New Scan.
- Enter:
- Scan Name / Tag
- Image Name (e.g.,
myapp/backend:v2) - Registry Type (ECR / ACR / GCR / Docker Hub / Private)
- Authentication Method (Connector / Manual Credentials)
- Optional Labels (Environment:
staging,prod)
- Choose Scanner Type (detailed in next section).
- Click Start Scan to begin.
View placeholder image for Creating a Container Scan

Scanner Selection
DeepTraQ supports multiple scanning engines optimized for different use cases:
| Scanner Type | Description | Primary Focus |
|---|---|---|
| Base Image & Package Vulnerability Scan | Scans system and language packages within container layers against CVE databases. | OS & library vulnerabilities |
| Dockerfile & Config Misconfiguration Scan | Analyzes Dockerfile, permissions, ENV variables, and best practices. | Security misconfigurations |
| Runtime Exposure Scan | Maps container services, open ports, and environment metadata (e.g., K8s node info). | Runtime exposure assessment |
| AI-Assisted Scan | Uses DeepTraQ's ML models to detect anomalous packages, secrets, or behavioral issues. | Advanced anomaly detection |
Managing Existing Scans
After creating a scan, navigate to the Container Scans list to view all configured scans in an expandable, accordion-style layout.
Each scan entry displays:
- Scan Name / Image Name
- Registry Type
- Tag / Digest
- Scan Status (Done, Running, Failed, Queued)
- Last Scan Findings (Critical, High, Medium, Low counts)
- Last Scan Time / Duration
- Base Image & OS
- Vulnerable Packages Detected
To view a reference image of existing container scans, click here to expand.
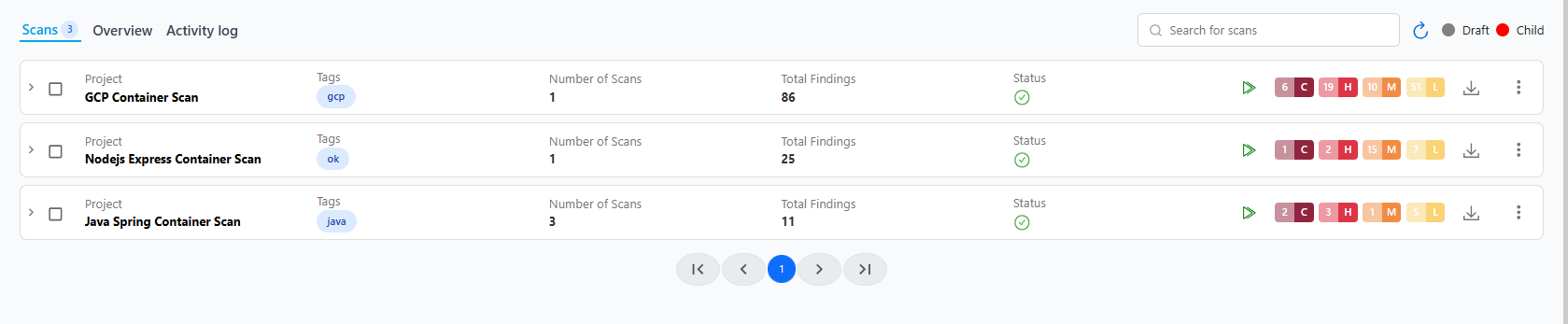
Use the **Run ** icon to re-run a scan, or the three-dot menu (⋮) to edit, duplicate, export, or delete.
Editing Scans
Editing allows you to modify:
- Image Name / Tag
- Registry Credentials
- Scanner Type
- Schedule
- Notification settings
Note: The registry type cannot be changed once the scan is created. Create a new scan if you wish to switch between registries.
Viewing Scan Results
Click on any Project (Scan Name) to view detailed scan results. The Container scan results dashboard consists of four main tabs:
- Summary
- Vulnerabilities (default tab)
- Attack Surface
- History
Summary
The Summary tab provides a high-level overview of the scan results, including:
- Total vulnerabilities found
- Severity distribution (Critical, High, Medium, Low)
- Total affected packages
- Base image details
- Registry and image tag
- Scan duration and completion status
Vulnerabilities
Displays detailed information about each detected issue.
Each finding includes:
- Vulnerability ID (CVE)
- Package Name & Version
- Severity (Critical / High / Medium / Low)
- Fixed Version (if available)
- CWE Mapping
- Base Image / OS Layer
- Affected Path
- Risk Description & Impact
- Remediation Guidance
- References (NVD / Vendor Advisory / Docker Docs)
Example:
- CVE: CVE-2024-45789
- Package:
openssl- Severity: High
- Fixed Version: 3.1.1-2
- Remediation: Update base image or rebuild with patched version
History
Shows a timeline of previous scans performed on the same image.
- Scan ID / Name
- Timestamp & Duration
- Scanner Type Used
- Total Vulnerabilities Found
- Comparison to Previous Scan (New vs. Resolved Issues)
Key Benefits
- Continuous visibility into container image security
- Automatic correlation with CIS Docker & Kubernetes Benchmarks
- Integration with registries and CI/CD pipelines
- AI-driven anomaly detection and prioritization
- Simplified compliance mapping (CIS, NIST, SOC2, HIPAA, GDPR)
Scanning Limits
- Each scan can evaluate up to 20 container or image scan in a single run.
- If scan finds more than one 20 images, it is split into multiple jobs each having 20 images and batched automatically and scheduled.
Launching a Scan
To manually run a container scan:
- Click the Run icon next to a scan in the list.
- This triggers an immediate container scan using the selected connector and selected scanner.
Scheduled scans will automatically execute at configured intervals (Daily, Weekly, etc.).
Email Notifications
Email alerts are automatically sent when:
- A Container scan starts or completes.
- A critical vulnerabilities are detected.
- A scheduled scan fails or misses execution.
Troubleshooting Scan Errors
If a scan fails, one of the following statuses may appear:
- Scan Submit Error: Scanner service temporarily unavailable or quota exceeded.
- Failed: Container scan check failed or timed out.
To diagnose:
- Open the scan.
- Navigate to the History Tab.
- Click the three-dot menu.
- Select Errors.
A detailed stack trace or message will appear for troubleshooting. Share this log with the DeepTraq Support Team for resolution.