Web Application Security
The Web Application Testing module in DeepTraQ allows you to scan and assess your web applications and APIs for vulnerabilities, misconfigurations, and insecure configurations. It supports both authenticated and unauthenticated scans to provide complete visibility into the security posture of web-facing assets.
This module can detect:
- OWASP Top 10 vulnerabilities
- Known CVEs and web server misconfigurations
- API-level issues such as missing authentication, weak validation, or broken access controls
- Behavioral anomalies using AI-based detection
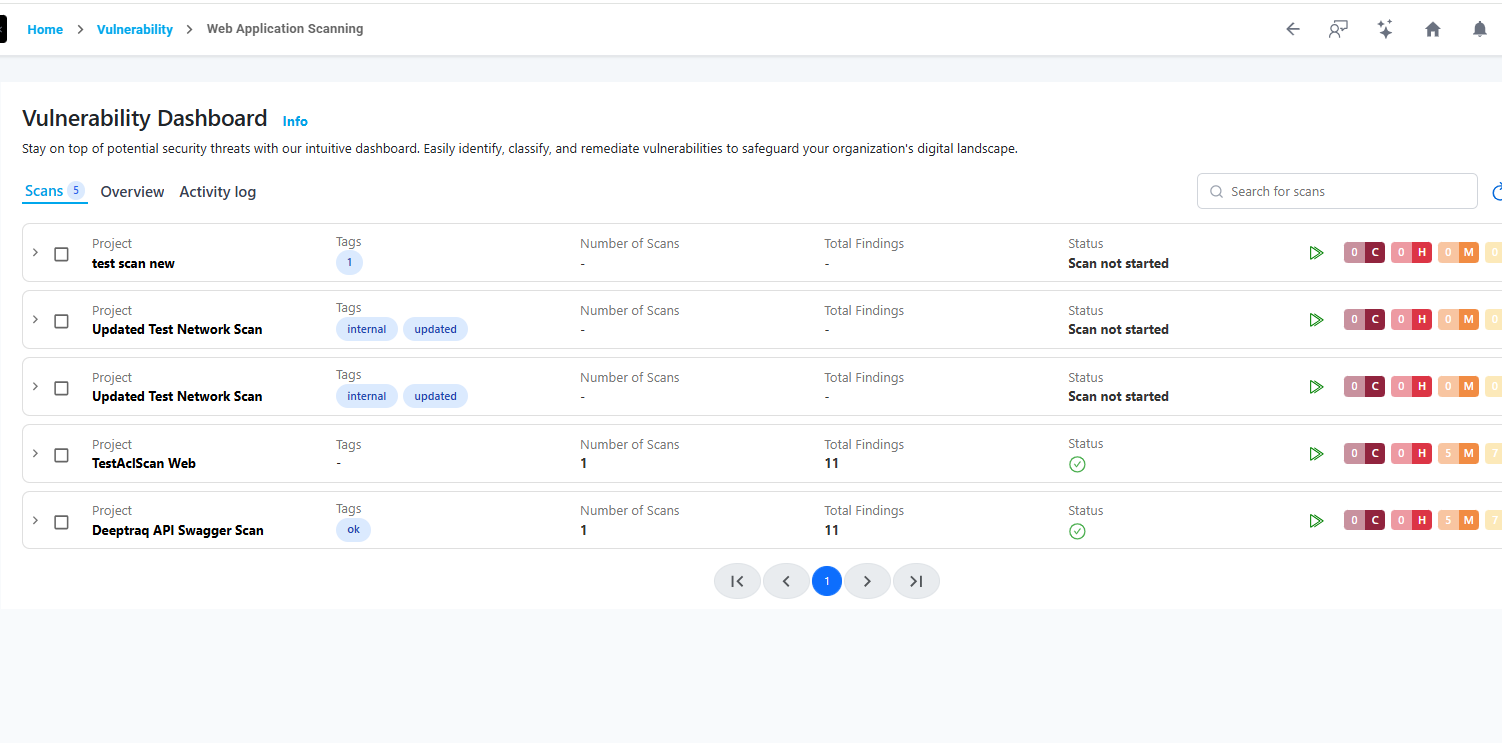
View placeholder image for Web Application Dashboard
How It Works
- Discovery Phase – The scanner crawls the target website or API endpoints to identify forms, parameters, and entry points.
- Testing Phase – Selected scanning engines analyze endpoints for known vulnerabilities, misconfigurations, or exposure.
- AI Correlation – AI engine classifies detected issues by severity, maps them to CWE and OWASP Top 10 categories, and eliminates duplicates.
- Reporting & Insights – Results are organized into Summary, Vulnerabilities, Ports & URLs, and History tabs for clear understanding and remediation tracking.
The scanning process is automated and supports integration with continuous monitoring workflows for ongoing web security management.
Requirements
| Requirement | Description |
|---|---|
| Target URL / API | Public or internal web URL reachable from DeepTraQ agents. |
| Authentication (Optional) | Username/Password, Bearer Token, or Custom Header-based authentication. |
| Swagger File (for APIs) | .yaml or .json format supported for API testing. |
| Connectivity | DeepTraQ agent must have access to target domain or endpoint. |
| Permissions | Read-only or testing-level access (no destructive actions are performed). |
Ensure your web application or API endpoints are reachable from the scanning agent's network and do not block user-agent strings used by DeepTraQ scanners.
Creating a Scan
- Navigate to Web Application Testing under the Application Security section.
- Click Create New Scan.
- Enter the following details:
- Website URL – e.g.,
https://app.example.com - Authentication – Optional username/password, bearer token, or full custom headers in JSON format.
- Scan Name / Tag – Optional metadata for organizing scans.
- Upload Swagger File (for API testing) –
.yamlor.json.
- Website URL – e.g.,
- Choose the Scan Type (detailed below).
- Click Start Scan to begin.
View placeholder image for Creating a Web Scan

Scanner Selection
DeepTraQ offers multiple web scanning engines based on target type and security requirement.
| Scanner Type | Description | Use Case |
|---|---|---|
| OWASP Top 10 Check Scan | Tests against OWASP Top 10 categories to find common web vulnerabilities such as XSS, SQLi, CSRF, SSRF, and more. | General web application scanning |
| Rapid Web Threat, Misconfig & CVE Scanner | High-speed scanner that detects known CVEs, framework misconfigurations, and outdated software versions. | Patch management and exposure analysis |
| AI-Based Web Application Scan | Machine learning-driven detection of unknown or behavioral anomalies. | Advanced web testing and zero-day identification |
| API Testing | Tests APIs using provided Swagger or OpenAPI definitions for authentication flaws, data exposure, and schema violations. | API-specific assessments |
For API scans, the input can be either a website URL or a Swagger file. If both are provided, the Swagger input takes priority.
Managing Existing Scans
After creating a scan, navigate to the Web applications list to view all created scans in a collapsible, accordion-style layout.
Each scan entry displays:
- Project (Scan Name)
- Scan Status (Done, Failed, Running, Partially Done)
- Last Scan Findings (Passed/Failed count)
- Severity Summary (Critical, High, Medium, Low)
To view a reference image of existing scans, click here to expand.
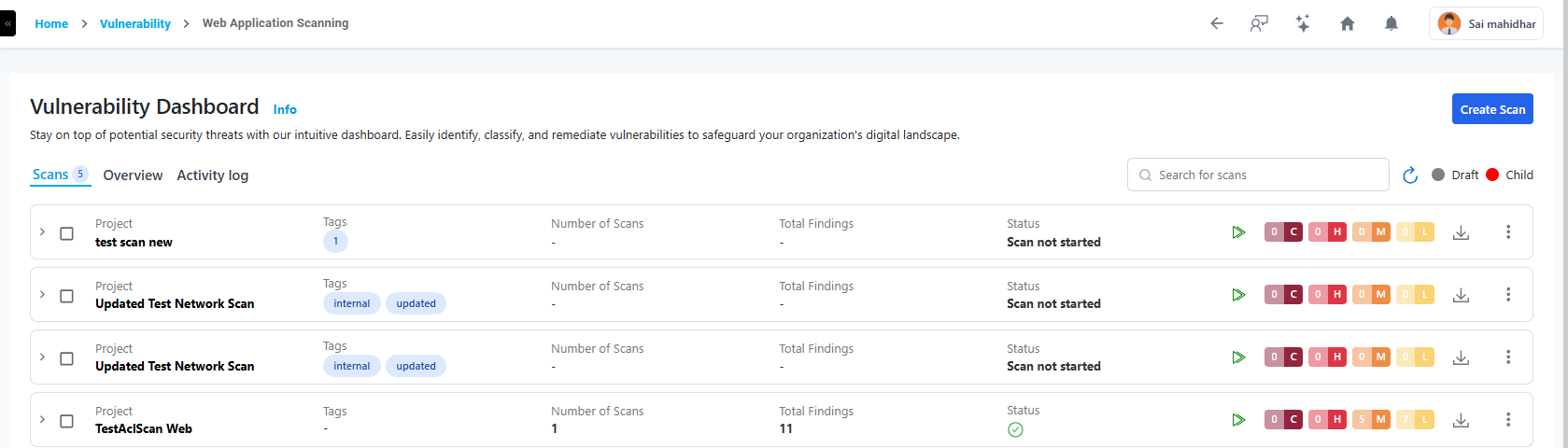
Use the Run icon to manually execute a scan, or use the three-dot menu to edit or delete.
Editing Scans
Editing allows you to modify:
- Scan Name / Description / Tags
- Target and Target credentials like Username, password, bearer token etc.
- Rule Set / Benchmark
- Scheduling options
Viewing Scan Results
The Web Application Testing results page consists of the following tabs:
- Summary
- Vulnerabilities (default tab)
- Ports & Crawled URLs
- History
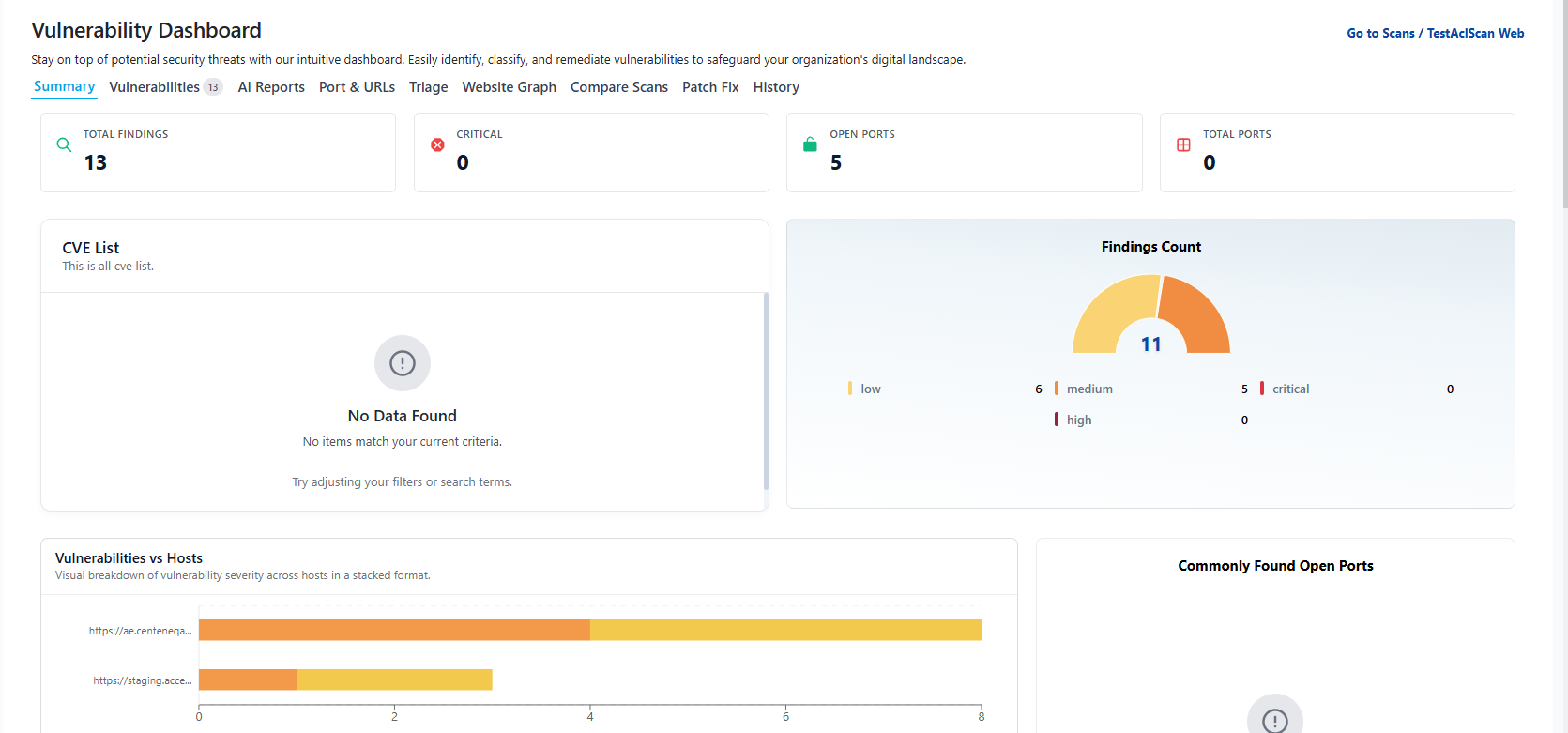
Summary
Provides an overview of the scan – status, duration, detected vulnerabilities count, open ports, and crawled URLs.
View placeholder image for Summary Tab
Vulnerabilities
Displays the discovered application vulnerabilities with detailed context and severity. This tab mirrors the structure of the Cloud Workload Vulnerabilities module.
Each vulnerability includes:
- Vulnerability Name & Description
- Severity Level (Critical / High / Medium / Low)
- CWE Mapping (Common Weakness Enumeration ID)
- OWASP Top 10 Mapping (e.g., A01 – Broken Access Control)
- Affected Endpoint / Parameter
- Proof of Concept or Evidence
- Remediation Guidance
- Detected On Timestamp
Example:
- Vulnerability: SQL Injection
- CWE: CWE-89
- OWASP: A03 – Injection
- Affected URL:
/api/user?id=1- Severity: High
Ports & Crawled URLs
Lists open ports detected on the web server and all discovered URLs during crawling.
- Open Ports: Useful to identify unnecessary exposed services (e.g., 8080, 8443).
- Crawled URLs: Enumerated endpoints, pages, and forms used for testing injection points and validation.
History
Maintains historical records of all previous web application scans with timestamps, duration, status, and total findings.
Users can easily:
- Compare results between runs
- Identify new vulnerabilities over time
- Re-run previous scans using the same configuration
Intelligent Insights
DeepTraQ automatically correlates web scan findings with known CWE and OWASP Top 10 categories for standardized reporting and compliance alignment. This provides consistent classification across vulnerability management and simplifies security audits.
Deleting a Scan
To delete a web application scan:
- Click the three-dot menu next to a scan → select Delete.
- Confirm by typing
DELETEin the popup confirmation dialog.
Scanning Limits
- Each scan can evaluate up to 1 website or 1 swagger file with 50 APIs in a single run.
- If scan having swagger file contains more than 50 APIs, it is batched automatically and scheduled.
Launching a Scan
To manually run a web application scan:
- Click the Run icon next to a scan in the list.
- This triggers an immediate web application scan using the selected connector and selected scanner.
Scheduled scans will automatically execute at configured intervals (Daily, Weekly, etc.).
Email Notifications
Email alerts are automatically sent when:
- A web application scan starts or completes.
- A critical vulnerabilities are detected.
- A scheduled scan fails or misses execution.
Troubleshooting Scan Errors
If a scan fails, one of the following statuses may appear:
- Scan Submit Error: Scanner service temporarily unavailable or quota exceeded.
- Failed: Web application check failed or timed out.
To diagnose:
- Open the scan.
- Navigate to the History Tab.
- Click the three-dot menu.
- Select Errors.
A detailed stack trace or message will appear for troubleshooting. Share this log with the DeepTraq Support Team for resolution.